EP-0149
TPM9670 Module for Raspberry Pi
Descriptions
TPM is an add-on GPIO TPM module for the Raspberry Pi platform based on an Infineon Optiga™ SLB 9670 TPM 2.0 . It is compatible with all Raspberry Pi models including the Raspberry Pi 4. Device tree overlay support with Raspbian Kernel >= 4.14.85 We offer customization services / custom designs starting at just 100 units. The module is compatible with Windows 10 IoT (on Pi 2 / 3). It is shipped with firmware versions >= 7.85 for TPM 2.0.
A TPM is a cryptographic processor present on most commercial PCs and servers. Ubiquitous in nature, it can be used for a wide variety of use cases, such as storing keys for VPN access and encryption keys for hard disks, or preventing dictionary attacks to retrieve private keys. While a typical TPM provides several cryptographic capabilities, three key features are relevant for this post:
- Establishing a root of trust
- Secure boot
- Device identification
Secure boot
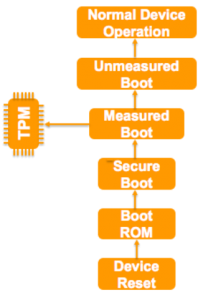
A secured boot builds on the underlying notion of a root of trust to protect the boot process from being compromised on the device. This whole process by which the trustworthiness of a device is established right from the chip is called a “Secure Boot”. In case a chain of trust is broken, the boot process is aborted and the device attempts to go back to its last known good state. An extension to secured boot process is a measured boot – where the device does not halt the boot process. Instead, it records the identity of each component that participates in the boot process so that these component identities can be verified later against a list of approved component identities for that device. This is called a measured boot. These two processes are illustrated in the following diagram.
Typical sequence of a measured boot
A typical sequence of a measured boot is as follows:
- The boot ROM acts as the root of trust.
- Upon a device reset, each image that forms part of the boot sequence is validated (measured) before execution.
- The measurements are stored in a TPM.
- Each measurement serves as the proxy for the root of trust for the subsequent step in the boot sequence.
- Normally, only critical and security-sensitive process and configuration files are considered for the measurement.
- After the security-sensitive processes are completed, the device enters the unmeasured boot stage before entering normal system operation state.
Device identification
In IoT solution deployments, it is important to check the identity of the device that is communicating with the messaging gateway. The usual method is to generate key pairs for the devices, which are then used to authenticate and encrypt the traffic. However, key pairs residing on the disk are susceptible to tampering. The TPM steps in here by storing the keys in tamper-resistant hardware. The keys are generated inside the TPM itself and are thereby protected from being retrieved by external programs. In fact, even without harnessing the capabilities of a hardware root of trust and secure boot, the TPM is also valuable just as a hardware key store. The private keys are protected by the hardware and offer far better protection than a software key.
Features
- Easy to install
- Infineon Optiga™ SLB 9670 TPM 2.0
- Compliant with TPM Specification 2.0 Rev. 01.38
- Firmware >= 7.85
- TRNG (Real Random Number Generator) - True Hardware Random Number Generator.
- Storing keys for VPN access
- Encryption keys for hard disks
- Preventing dictionary attacks to retrieve private keys
Gallery
- Product Outlook:
- Product Details:
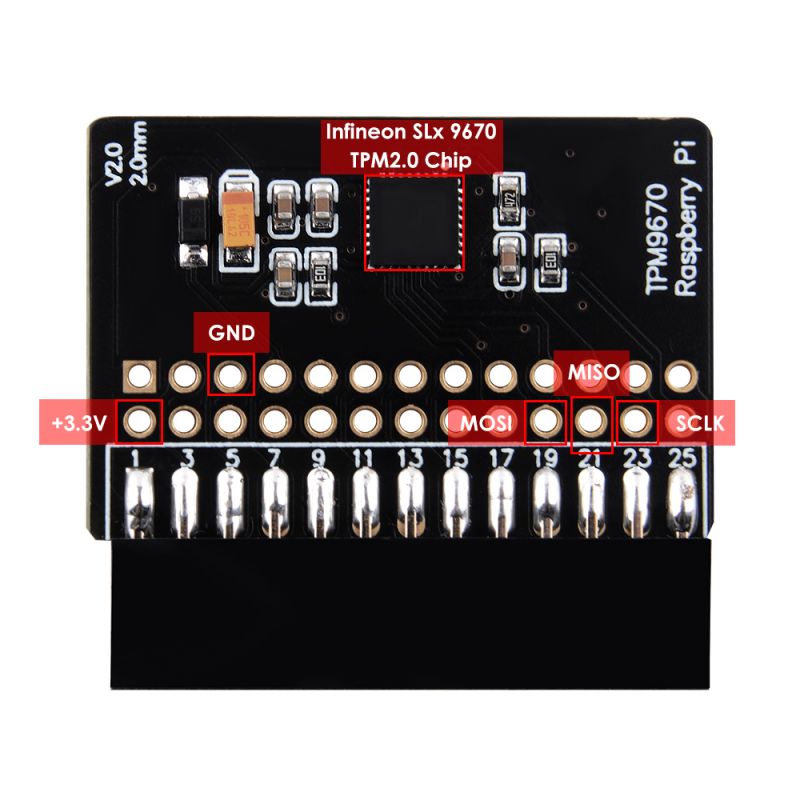
- Pinout definitions:
Package Includes
- 1 x TPM9670 Module for Raspberry Pi
How to use
This integration requires the following components:
- A Raspberry Pi running Raspbian Stretch.(Raspberry Pi 4B will be better.)
- Infineon TPM9670 module(SLB 9670)
- OS info: Raspbian GNU/Linux 10 (buster)
- Kernel Version: 5.10.17-v7l+ #1421
- Device info: Raspberry Pi 4B 4GB
Getting Start
- The Infineon OPTIGA TPM uses the SPI interface to connect to the Pi on the GPIO Pins. Once the OPTIGA™ TPM is plugged into the PI, it should look as follows:
On the top is the Raspberry Pi® Header with 26 pins.
The Raspberry Pi® 4 Header has VDD, GND, MOSI, MISO and SCLK at the following pins:
| Pin | 1 | 6 | 19 | 21 | 23 |
|---|---|---|---|---|---|
| Signal | +3.3V | Gnd | MOSI | MISO | SCLK |
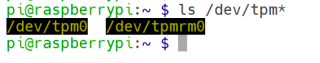
- Go through the following steps to validate the initial setup of the TPM and to check if the Raspberry Pi is able to recognize the TPM on reboot, Reboot your Raspberry Pi and check that /dev/tpm0 is available.
- Update your system with the following command:
sudo apt update && sudo apt upgrade
- Install latest kernel using the following command:
sudo rpi-update
- Edit /boot/config.txt and add the following line:
dtoverlay=tpm-slb9670
- Enable SPI via using `raspi-config` tool, navigate to `Interface Options` -> `SPI` -> `Enable` -> `YES`:
sudo raspi-config
- Reboot Raspberry Pi after configuring.
sudo reboot
- Check if `/dev/tpm0` is available.
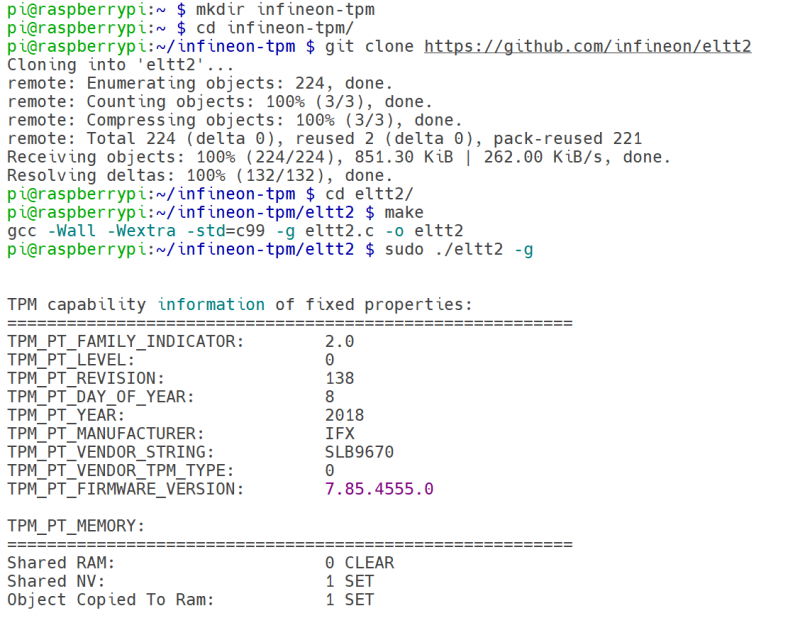
- A detailed verification can also be done by running a small utility, eltt2, provided by Infineon Technologies AG and available on GitHub. All of the following setup packages are created and built under the infineon-tpm directory.
mkdir infineon-tpm cd infineon-tpm/ git clone https://github.com/infineon/eltt2 cd eltt2 make sudo ./eltt2 -g cd ..
This output confirms that the TPM is working correctly.
Enable TPM reference in the app
For a TPM to function, it requires a complete software stack including drivers, resource managers, and other tools. Each of these components is available from GitHub (see links in the following sections) and has been built to the specifications laid out by the Trusted Computing Group (TCG). These software components include:
TPM TSS Library: This library consists of the TCG’s TPM2 Software Stack (tpm2-tss) specification. This library comprises various software components that implement the low-level and high-level APIs, transmission of commands to the TPM, and the marshalling and un-marshalling of all the data structures defined by the TPM2 specification. TPM PKCS#11: The PKCS#11 is a public key cryptography standard that defines a standard method to access cryptographic services from tokens or devices such as HSMs or smart cards. In this example, the Infineon TPM serves as the HSM. TPM2 Access Broker and Resource Manager: These are system daemon processes that implement the TPM2 Access Broker (TAB) and Resource Manager (RM) spec from the TCG.
Documentations
- Infineon OPTIGA SLx9670 TPM 2.0 Pi 4 Application Note: File:Infineon-OPTIGA SLx 9670 TPM 2.0 Pi 4-ApplicationNotes-v07 19-EN.pdf
- TPM Software: [ https://github.com/tpm2-software ]
- ELTT2 tool: [ https://github.com/Infineon/eltt2 ]
- Useful scripts: [ https://github.com/PaulKissinger/LetsTrust ]
- Work with AWS Greengrass IoT : [ https://aws.amazon.com/cn/blogs/iot/using-a-trusted-platform-module-for-endpoint-device-security-in-aws-iot-greengrass/ ]
- Datasheet: [ https://www.infineon.com/dgdl/Infineon-OPTIGA_TPM-PB-v10_15-EN.pdf?fileId=5546d46145da30e80145efa2f0b96a8e ]
- Datasheet(HTML): [ https://www.digikey.cn/zh/htmldatasheets/production/2078094/0/0/1/optiga-tpm-brief.html ]
- How to enable TPM module for windows 11: [ https://www.wepc.com/how-to/enable-tpm-for-windows-11/ ]
Keywords
- TPM9670 Module, Trusted Platform module, Raspberry Pi, SLB 9670, SLI 9670 and SLM 9670